This chapter will cover the following topics
- Basics of Authentication and authorization
- Introduction of IAM
- Elements of IAM
- Creating and managing Users
- Creating and managing Groups
- Creating and managing Role
- Policy and policy classification
- Managed policy v/s resource based policy
- Few terminologies regarding policy
- Example of customer managed policy
- Example of resource based policy
- Overview of Active Directory Federation Services(ADFS)
- Overview of Web Identity Federation
- Overview of Security Token Service(STS)
- AWS CLI command respect to IAM
Basics of Authentication and authorization

Authentication:
- It is the process of verifying who you are.
- When you log on to a PC with a user name and password, you are authenticating.
- Authentication is about who somebody is.
Authorization:
- It is the process of verifying that you have access to something.
- Gaining access to a resource (e.g. directory on a hard disk) because the permissions configured on it allow you access is authorization.
- Authorization is about what they’re allowed to do.
Introduction of IAM
- IAM is a global service. Not a region specific.
- It is a free service. No limitations.
- It is specially designed to create and manage users, groups, roles and policies for securely controlling access to various AWS resources.
- I – Identity – Identity to authorize someone
- A – Access – Authority to access or to do something
- M – Management
- It controls
- who can use your resource – Authentication
- what resources that can use in what ways – Authorization
AWS Root User:

- When you create an account, it will automatically create a root user.
- Root account credential = email address + password used while creating an account.
- Root user has complete and unrestricted access on AWS services.
- Root user’s permission cannot be altered by any other user.
- On a newly created AWS account, it is recommended that you create individual IAM users based on the organizational need and assign the required permissions.
- These non-root user accounts should be used for day-to-day activities.
Elements of IAM

Real-life organizational users and their permissions to access AWS resources as per their roles and responsibilities.
User:
Any person/application
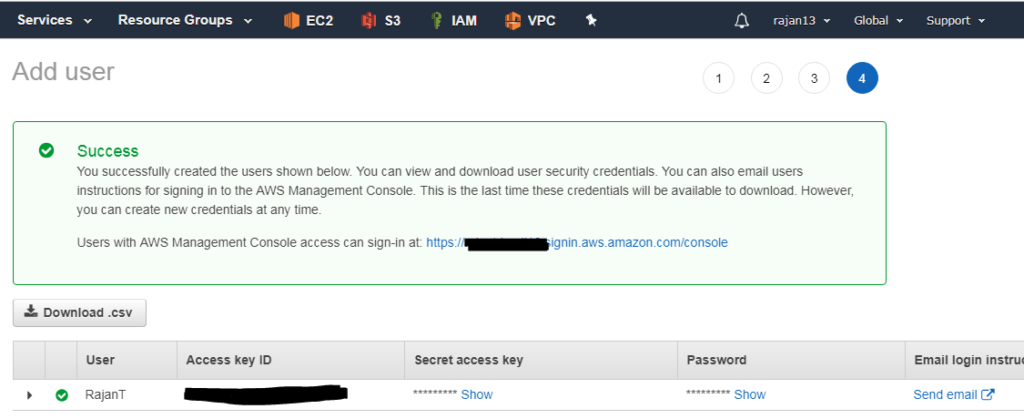
A user can access AWS resources with either a username and password or with an access key and secret key.
Access Key:
An access key is a 20-character alphanumeric key that acts as a user ID.
Secret Key:
A secret key is a 40-character alphanumeric key that acts as a password or secret key.
The access key and secret key are used together for initiating API, SDK, and CLI authentication.
Password policy:
It specifies the complexity requirement of a password and defines the mandatory rotation period for a password associated with IAM users.
Multi-Factor Authentication (MFA):
It is an extra layer of security protection for user authentication that requires users to enter a six-digit token on top of the username and password.
Group:
It is a collection of IAM users.
Role:
It does not have any identity credential with it.
It required one or more IAM policies that define permission.
Policy:
It is a document written in JSON format that formally states one or more permissions as per the IAM policy standards.
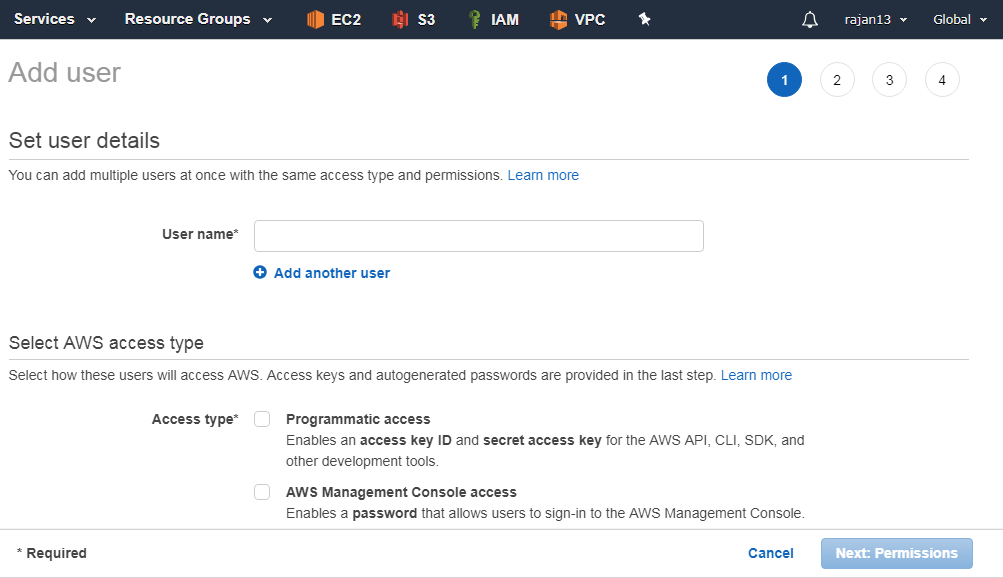
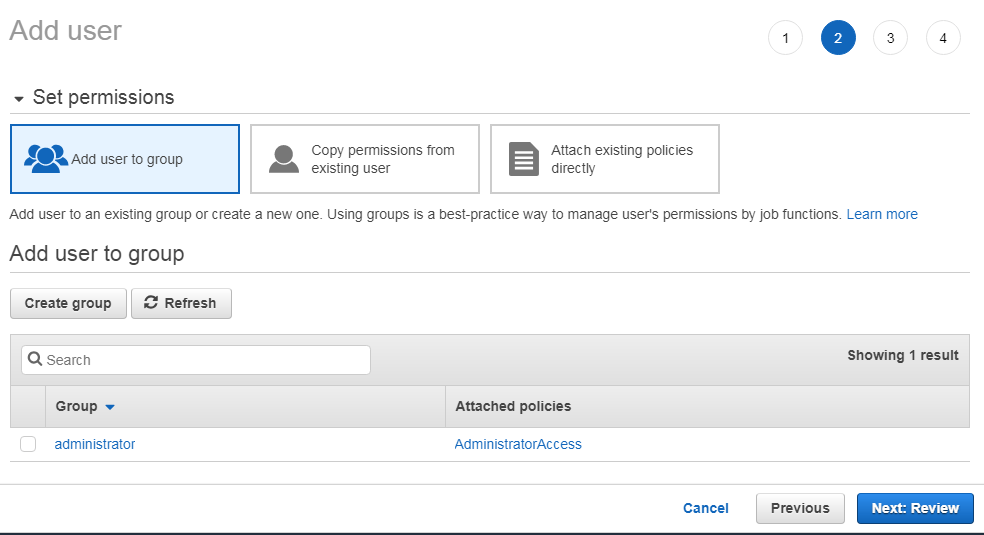
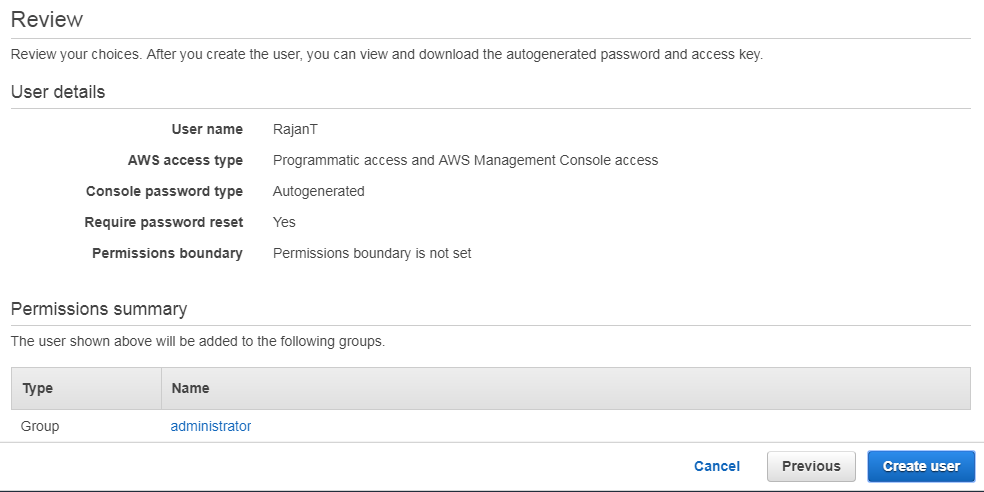
Creating and managing users

Users can be actual user or application.
Usually, an individual user is authenticated by username and password.
Similarly, programmatic access (that is SDKs and CLIs, also known as applications) are authenticated using an access key and secret key.
By default, access key and secret keys are not generated for all users.
It is recommended to generate access key and secret key only for those users who want to access AWS resources via API,CLI or SDKs.
By default, the only root user has billing access.
Newly created user does not have any privileges in AWS, unless and until you attach proper policies.
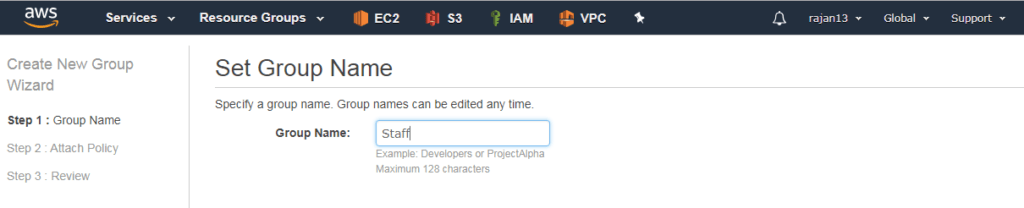
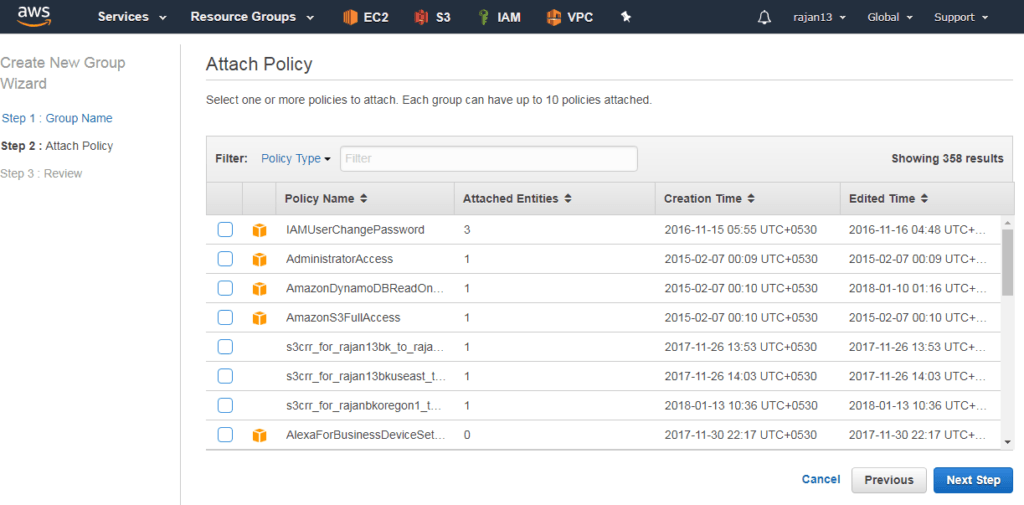
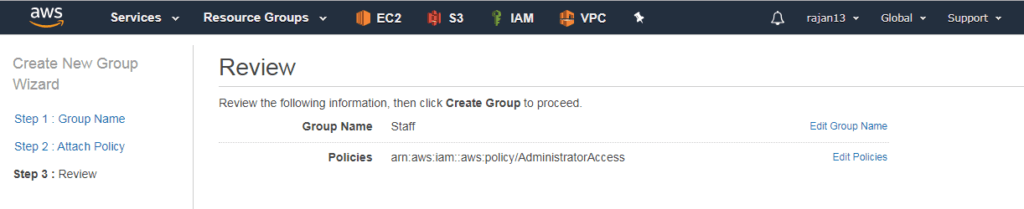
Creating and managing groups

Any group have many users and one user can be a member of many groups
Groups can not be nested. It means one group can not be a part of another group
By default, the user is not a part of any group
By default soft limit is: 100 IAM groups and 5000 users
Group name length up to 128 chars. long
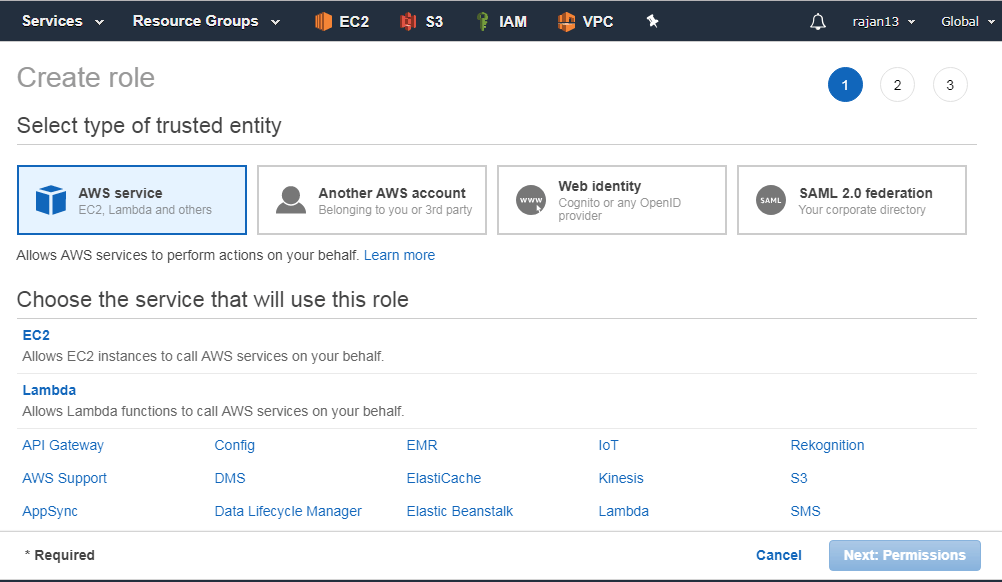
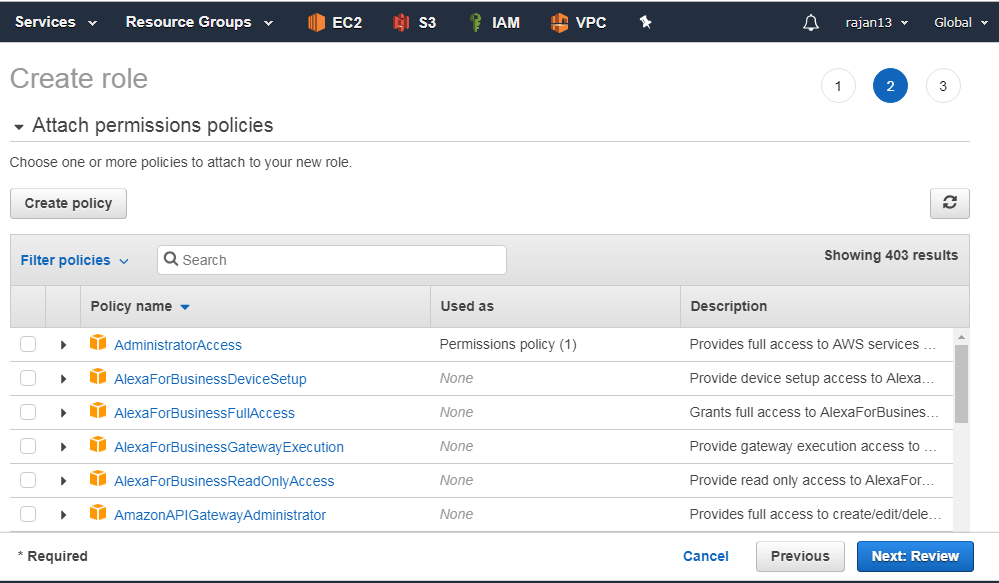
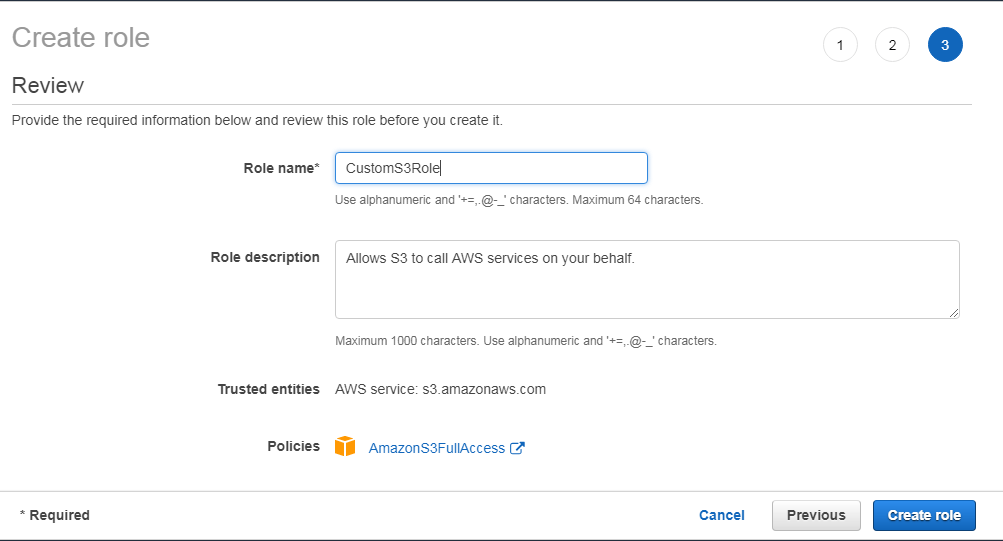
Creating and managing role

Role is AWS identity
IAM policies can be associated with IAM user or IAM group
IAM role cannot be associated with user or group
Role name – up to 64 chars
It is recommended that AWS resource permission in the form of IAM policies are attached to an IAM role rather than being attached to IAM users or groups.
Policy and Policy Classification
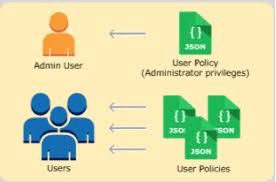
Policy:
Policy is a JSON document that stats one or more permissions to access AWS resources
A policy can be associated with one or more IAM users, groups, roles and resources.
Policy Classification:
Managed policy:
Customer managed policy
AWS managed policy
Inline policy:
Customer managed policy with 1 to 1 mapping between policy and principal.
Directly can be attached with a single user, group and role.
Resource based policy:
It is an inline policy but specific to any AWS service/resource.
Managed policy v/s resource based policy
The major difference between a managed policy and a resource-based policy is –
A resource based policy specifies who has access to the resource (principal) and list of permitted actions, whereas in managed policies the only list of actions is specified, not the principal entity.
An IAM resource-based policy can also be generated with the help of the AWS policy generator.
The URL for the AWS policy generator is https://awspolicygen.s3.amazonaws.com/policygen.html
Few terminologies regarding Policy
Version:
Specifies IAM policy language version.
The latest and current version is 2012-10-17. It should be used for all the policies (that is, managed or resource-based policy).
Effect:
It defines whether the specified list of actions in Action elements on specified resources specified in Resource elements are allowed or denied.
By default, every service and resource is denied access. Usually, policies are written to allow resource access.
Actions:
This defines a list of actions.
Each AWS service has got its own set of actions.
Resources:
This section specifies the list of resources on which the preceding specified list of actions is allowed.
{
"Version": "2012-10-17",
"Statement": { "Effect": "Allow", "Action": "s3:*", "Resource": "arn:aws:s3:::mybucket" }
}
Amazon Resource Name (ARN) is a unique identifier for each of the AWS resources.
It is used in IAM policies, API calls, and wherever it’s required to identify AWS resources unambiguously.
A basic example of ARN is as follows:
arn:partition:service:region:account-id:resource
arn:partition:service:region:account-id:resourcetype/resource
arn:partition:service:region:account-id:resourcetype:resource
Example of resource based policy
{
"Version": "2012-10-17",
"Statement": { "Sid": "AccountBAccess1", "Effect": "Allow", "Principal": {"AWS": "111122223333"}, "Action": "s3:", "Resource": [ "arn:aws:s3:::mybucket", "arn:aws:s3:::mybucket/" ]
}
}
{
"Version": "2012-10-17",
"Statement": { "Effect": "Allow", "Action": "s3:List", "Resource": [ "arn:aws:s3:::mybucket", "arn:aws:s3:::mybucket/" ]
}
}
In the first policy,
Here, account A’s S3 bucket is named mybucket, and account B’s account number is 111122223333.
It does not specify any individual users or groups in account B, only the account itself.
In the second policy,
To implement this policy, account B uses IAM to attach it to the appropriate user (or group) in account B.
Means user B only mention the bucket name of user A.
Overview of Active Directory Federation Services(ADFS)
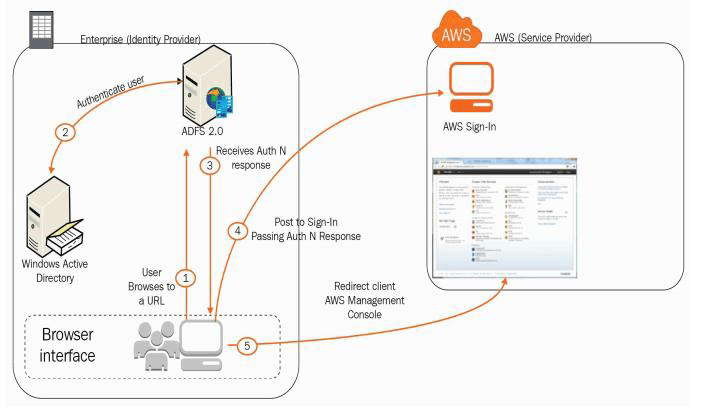
External identities are called Federated users(Not permanent users)
Federated users are granted secure access to your resources without creating IAM users
We cannot attach policies to unknown users
So, login with the organization’s AD that provides token-based SSO service for accessing systems and applications
Overview of Web Identity Federation
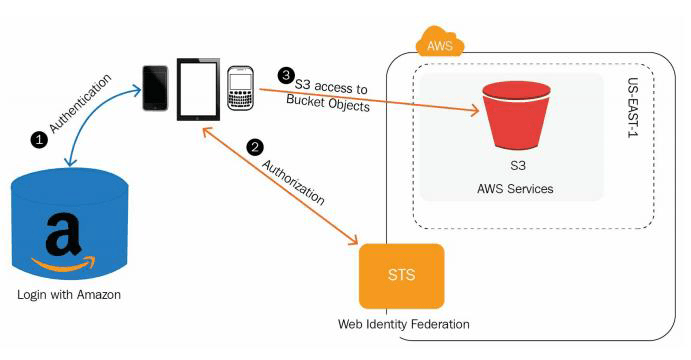
While mobile app wants to access AWS resource then, authentication using access key and the secret key is not recommended due to security aspects.
We have an option called – web identity federation
The application can request temporary security credentials dynamically when required from STS
Here, no need to create own custom sign-in code, you can log in through Facebook, Amazon, Google etc.
Overview of Security Token Services(STS)
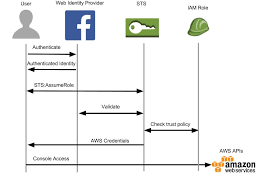
It is a global web service which enables an application to dynamically generate temporary security credentials either for federated users or IAM users.
URL for global service STS – https://sts.amazonaws.com/
AWS CLI commands respect to IAM
CLI is a unified tool to manage AWS resources.
First, you need to download CLI in your system from https://docs.aws.amazon.com/cli/latest/userguide/awscli-install-windows.html
Install CLI by double clicking on that package.
Once installed, open command prompt and perform the following steps to configure CLI with your AWS account:
C:\Users\Rajan>aws configure
Root user credentials:
AWS Access Key ID [None]:
AWS Secret Access Key [None]:
Default region name [None]: us-east-1
Default output format [None]: json
Now, you have successfully configured CLI in your systems, you can perform CLI commands now.
CLI commands general syntax:
aws
aws help
aws iam help
aws iam create-user –user-name testadmin
aws iam create-group –group-name julybatch
aws iam delete-user –user-name testadmin
aws iam delete-login-profile –user-name testadmin
aws iam detach-user-policy –user-name Bob –policy-arn arn:aws:iam::123456789012:policy/TesterPolicy
CLI commands for all AWS services can be found at:
https://docs.aws.amazon.com/cli/latest/reference/
Summary
In this chapter, we have seen one of the important services of AWS that is IAM.
Stay tuned with me for the next chapter related to storage Services that is: Simple Storage Service(S3).



